Cybersecurity
Cybersecurity is the frontline defence in India’s digital age, protecting businesses, governments, and individuals from the rising tide of cyber threats, data breaches, and online frauds in 2026 and beyond. At Three Windows, our Cybersecurity category is your trusted resource for navigating the complex world of digital security with practical tips, expert insights, and the latest trends tailored for Indian readers.
What This Category Includes
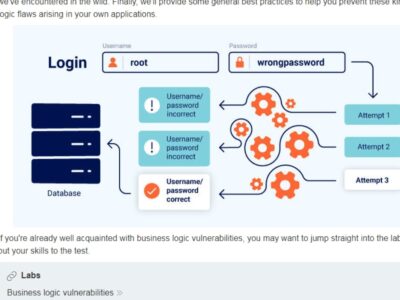
Explore detailed articles, tutorials, and guides on essential cybersecurity topics like threat detection, network security, data encryption, ransomware prevention, endpoint protection, and incident response. Our content also covers cybersecurity compliance, the implications of India’s Digital Personal Data Protection (DPDP) Rules 2026, and how to secure cloud infrastructure, IoT devices, and fintech platforms. You’ll find strategies to protect your startup or enterprise from modern cyberattacks using best practices and real-world case studies relevant to India.
Why Cybersecurity Matters Now
With India’s accelerating digital transformation, cybercriminals are becoming more sophisticated, using AI-driven attacks, phishing scams, and supply chain breaches to exploit vulnerabilities. Cybersecurity is no longer optional; it’s a critical business function that safeguards reputation, customer trust, and regulatory compliance. The DPDP Rules have raised standards for data privacy and protection, guiding businesses to adopt robust security architectures and proactive monitoring.
What You Gain Here
Each piece is designed to empower entrepreneurs, business managers, IT professionals, and everyday users with easy-to-understand security frameworks, how-to guides, tool reviews, and risk mitigation tactics. Stay ahead with the latest updates on cyber laws, security technologies, threat intelligence, and Indian market-specific security challenges.
Secure your digital future today by exploring Three Windows’ Cybersecurity content – your partner in building a safer and resilient digital India.